For Developers
Find and evaluate open source packages
Trusty provides a free-to-use service with scoring and metrics about a package’s repo and author activity.
Trusty provides a free-to-use service with scoring and metrics about a package’s repo and author activity.
Malicious attacks are becoming more sophisticated, and AI is making it easier and faster for attackers to execute them. We need new ways to detect and prevent supply chain attacks. Stacklok is developing new tools and approaches, in alignment with open source communities.
Minder Cloud helps open source developers and communities use open source security tools and standards to continuously secure their software projects, and provide proof of that security to their downstream consumers.
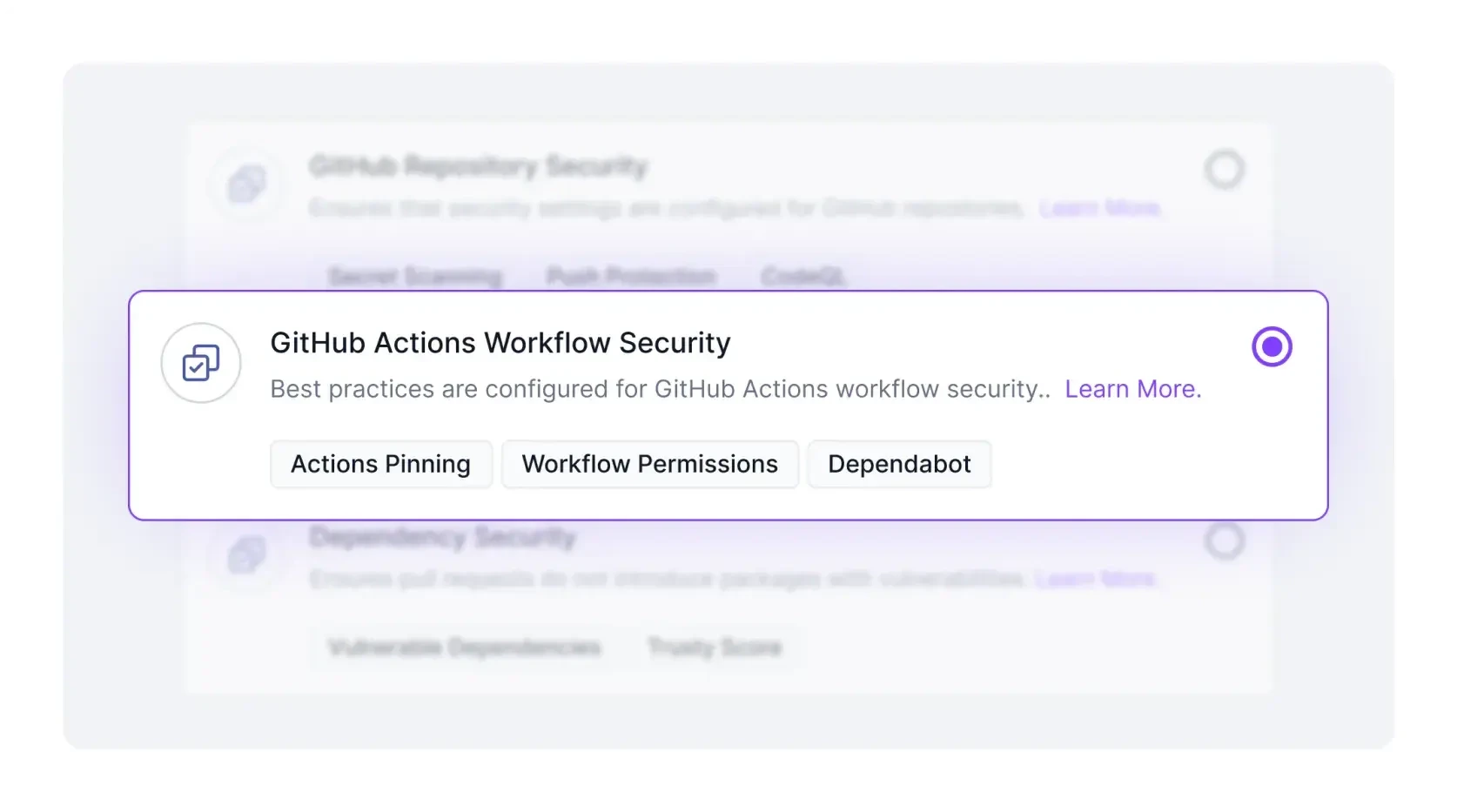
No more manual configuration and spreadsheets. Use Minder Cloud to apply and consistently enforce the same set of policies across a group of project repos.
Minder flags dependencies in pull requests that have known CVEs or high supply chain risk, and provides a list of safer alternatives to help developers find a different package to use.
Implement GitHub-recommended best practices like limiting workflow permissions and pinning actions to commit SHAs (Minder can even do this automatically for you!).
Daniel Finneran
Isovalent
"We had well over 100 repos at one point, and all needed some level of review. It would be ideal to be able to set a basic security standard for repos, automate as much as possible, and have remediation steps."
Trusty makes it easier for developers to understand whether an open source package is authentic, non-malicious, and actively maintained. It's free to use and accessible as a web app and as a Visual Studio Code extension.
Get quick signal with our Trusty Score, which establishes a benchmark for average levels of activity based on statistical analysis of public GitHub package data.
When artifacts have been signed using Sigstore, Trusty displays a verifiable chain of trust back to the source code so that you know the package is what it says it is.
Trusty uses generative AI to provide a list of related packages and their scores, so that you can find and evaluate other packages if you need a safer option.
Matt Klein
Founder, Envoy proxy
“Package activity is a key predictor of its health and safety. That's why Envoy's policy on external dependencies includes evaluation factors like number of commits in the last 90 days, release notes, and whether other projects depend on it, so that we can make safe choices."
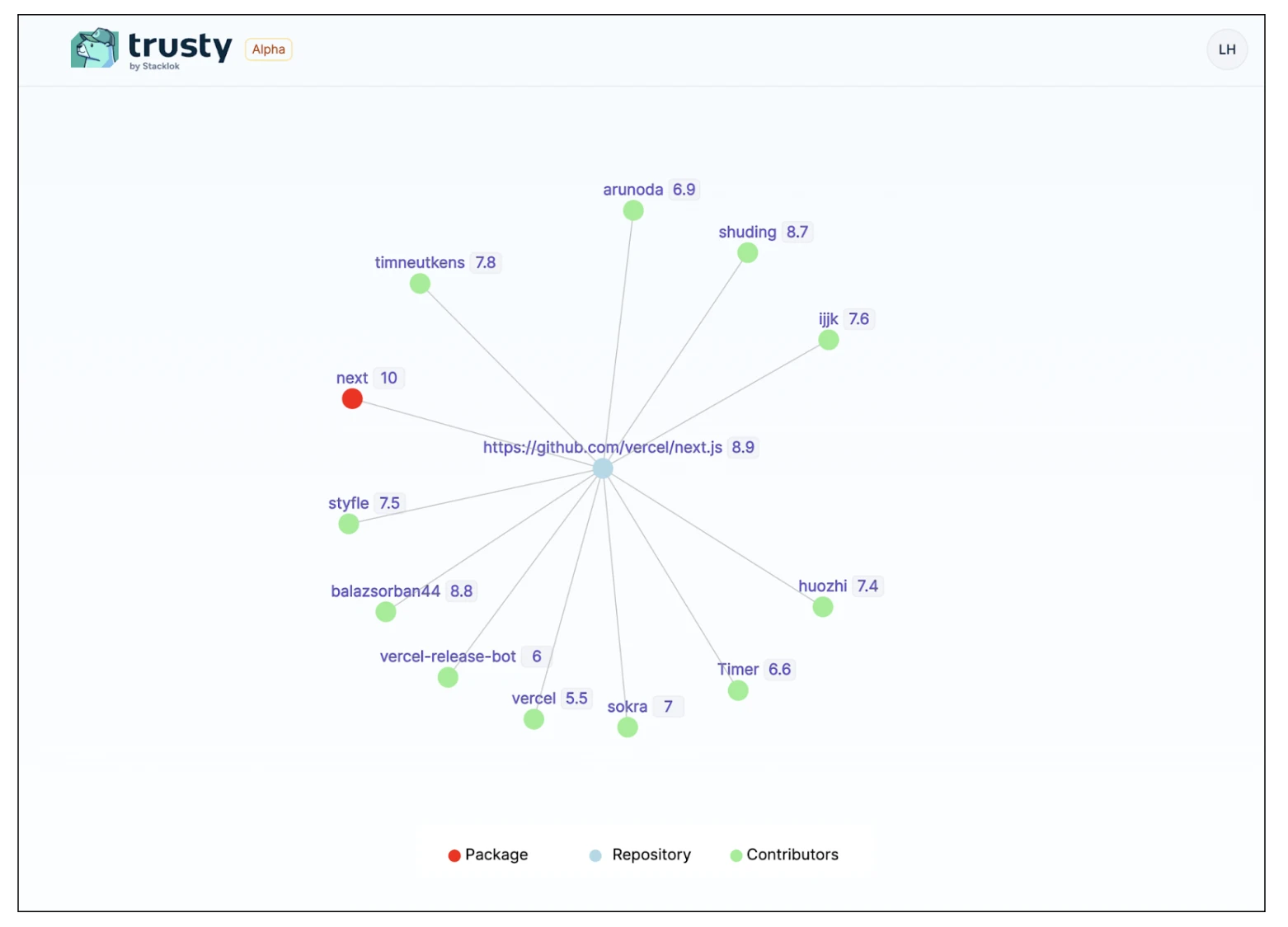
Above: Prototype of the Package Graph view of the next.js project
The OSS Trust Graph, a new capability of Trusty, is a way to model trust in open source ecosystems. It maps the connections between open source contributors and projects, and, through a “proof-of-diligence” algorithm, uses that data to build an understanding of the relative safety and sustainability of those projects.
It can be used to:
Identify malicious activity: Identify when a number of relatively unknown individuals start to contribute to the same project, or when the behavior of a maintainer changes
Identify open source projects that need support: Identify when a high-contributing maintainer leaves a project, leaving it vulnerable; or when a high-scoring project has a low number of maintainers and could benefit from support and funding

A free weekly newsletter about software supply chain security. We cover security incidents, security tips, free and OSS tools, and updates on community and public sector initiatives you should know about. Brought to you by Stacklok.


